FEDS Notes
May 12, 2022
Implications of Cyber Risk for Financial Stability
Danny Brando, Antonis Kotidis, Anna Kovner, Michael Lee, and Stacey L. Schreft1
Cyber risk, defined as the risk of loss from dependence on computer systems and digital technologies, has grown in the financial system. Cyber events, especially cyberattacks, are among the top risks cited in financial stability surveys in the United States and globally.2 Similar to other financial vulnerabilities, cyber risk presents both micro and macroprudential concerns However, while substantial technical attention has been paid to cyber resilience, measuring the ramifications of cyber risk for the financial system is at an early stage.
This article proposes a way to assess the vulnerability of the financial system to cyber risk. The approach aligns with the existing Federal Reserve financial stability framework, focusing on how a cyber shock could be amplified by the financial system and on how to monitor the vulnerabilities that lead to that amplification.
We offer three conclusions. First, cyber risk can be considered in the Federal Reserve's financial stability framework, but traditional mitigants such as capital and liquidity may need to be supplemented by other interventions to limit systemic effects of cyber shocks. Second, more research is needed to understand the transmission channels and mitigants for cyber vulnerabilities. Finally, significant data gaps impede assessing and mitigating cyber vulnerabilities, both within the financial system and at service providers.
While improving firm-level cyber resilience is critically important, the focus of this article is on financial stability and the potential for amplification through the financial system, not on microprudential supervision.
Cyber Risk as a Financial Stability Vulnerability
Cyber risk in the financial system has grown over time as the system has become more digitized, as evidenced by the increase in cyber incidents. That growth has brought to light unique features of cyber risk and the potentially greater scope for cyber events to affect financial stability. Understanding financial stability vulnerabilities emerging from cyber is critical because capital and liquidity may not mitigate the effect of a cyber event in the same way they mitigate financial losses.3 For instance, capital and liquidity can provide the financial resources to respond to a cyber incident but may not speed the process of recovering systems or data.
Cyber risk is more likely to be realized with systemic ramifications than is operational risk generally. Fire sales, liquidity freezes, and potential solvency issues may play out differently after a cyber shock. For example, if a cyber incident compromises a financial institution's data, the firm's ability to service creditors might be impaired. An inability to withdraw may mitigate the implications of a run for the affected institution, but customers may run on other institutions fearing lack of access to accounts. Enhancements in service offerings, such as longer operating hours of payment systems and shorter clearing and settlement windows, have left the financial system with fewer service breaks in which operations can be restored after a cyber incident. Rehypothecation and more complex derivatives mean that greater volumes of transactions depend on instantaneous information flow. Uncertainty about the nature and extent of an incident may prompt runs on counterparties, competitors, or unaffected segments of the firm's operations. The 2021 ransomware attack on Colonial Pipeline, though not a financial firm, illustrates how a cyberattack can spark a run (in this case, a run on gas stations), amplifying the effects well beyond the original shock (in this case, on fuel distribution).
Another factor distinguishing cyber risk is that shocks may spread through the financial system through complex and often unrecognized connections across firms, including a layer of exposures to shared technologies and third-party service providers. This layer is in addition to the connections from financial payments and exposures typically captured in measures of counterparty risk.
Increased market concentration, whether from digital economies of scale or other market forces, can result in single, or near-single, points of failure and increased financial system vulnerability to cyber shocks.4 For example, the overall increased concentration in the U.S. banking industry means that an increasing number of banking markets and products are served by relatively few banks. In addition, digital consolidation and its associated risks are apparent in the provision of some key services, including Treasury clearing and settlement and cloud-service provision. Increased transactions through central clearing counterparties (CCPs) also represent increased concentration risk. CCPs have reduced some vulnerabilities that were prominent in the 2008-09 financial crisis by increasing transparency and netting, with accompanying capital and liquidity savings, but they also may increase cyber vulnerability by concentrating activity in a single entity, depending on the investment in cyber resilience.
Even with considerable investment in resilience, given the cyberattack capabilities of nation states, the financial system is likely more vulnerable to a cyberattack when the system has fewer redundancies. This highlights the final, and perhaps more significant, difference of cyber risk from other financial stability risks—the possible intentional nature of events. While most cyber events the U.S. financial system has experienced thus far have had a profit motive, threat actors with malicious intent can target one or more firms or parts of the critical infrastructure and time their attacks to better exploit vulnerabilities and have systemic effects.
Of course, there are similarities between cyber and other financial system shocks. Cyber shocks can lead to losses hitting many firms at the same time because of correlated risk exposures (sometimes called the popcorn effect), such as when firms load the same malware-infected third-party software update. And the interconnectedness of the financial system means that an event at one or more firms may spread to others (the domino effect). For example, a cyber event at a single bank can disrupt the bank's ability to send payments and have cascading effects on other banks' liquidity and operations. Finally, individual firms (including those in the supply chain) will underinvest in their own resilience, failing to internalize their effect on the system's stability and thus putting the system at more risk than is optimal.
Cyber in the Federal Reserve Framework
The Federal Reserve's financial stability monitoring framework distinguishes between shocks to and vulnerabilities of the financial system (Board of Governors of the Federal Reserve System 2021). In that framework, shocks are sudden and typically unexpected changes to financial or economic conditions. In contrast, vulnerabilities build gradually over time and are the aspects of the financial system most expected to cause problems in times of stress. Table 1 shows how the framework translates to approaches to considering cyber risk and financial stability.
Table 1. Transmission of Cyber Shocks to Affect Financial Stability
| Shocks | Vulnerabilities | Implications | |
|---|---|---|---|
| Firm Level | System Level | ||
| Cyber events are occurrences, malicious or not, within an information system or network | Weaknesses in a firm’s controls, defenses, and recovery ability can allow cyber events to become cyber incidents, impairing operations (for example, by causing a loss of funds or data; corrupting data; halting operations; or causing other monetary or reputational losses) | Financial system features (for example, interconnections from financial and digital exposures; data and operational dependencies; market concentration and lack of substitutes for critical services; time sensitivity; confidence) can amplify and spread a cyber incident to disrupt the system’s functioning | Incidents that sufficiently disrupt the financial system’s functioning can affect financial stability (for example, by causing a lack of availability of critical services or data, runs and asset fire sales, lack of access to funding, or disrupted payments or price discovery) |
Shocks associated with cyber risk are cyber events—occurrences, whether malicious or not, in an information system or network. Cyber events can be external or internal in origin. As with any economic or financial shock, a cyber event need not affect financial stability. In fact, most cyber events at financial firms are thwarted by firm controls and defenses, such as regular software patching and maintenance of strong network firewalls.
For a cyber event to affect financial stability, it must first exploit firm-level vulnerabilities so that the event becomes an incident—an event that impairs the firm. Firm-level vulnerabilities are weaknesses in a firm's cybersecurity and its ability to recover from a cyber event before damage is done. Potential adverse firm-level effects include a loss of funds or data, data corruption, disrupted operations, and monetary or reputational costs.
System-level vulnerabilities are features of the financial system that can amplify and spread a cyber incident so that the incident disrupts the system's functioning. Examples of system-level vulnerabilities include interconnectedness from financial and digital exposures, data and operational dependencies, markets with dominant firms and a lack of available substitutes for critical services, the time sensitivity of payments, and the level of confidence in financial relationships. A significant cyber incident may reveal additional channels through which cyber risk impacts the financial system.
Cyber incidents that sufficiently disrupt the financial system's functioning can affect financial stability. Consequences could include a lack of availability or accessibility of critical services, data, or funding; a loss of confidence, resulting in runs and asset fire sales; or disruptions to payment flows or price discovery. Less significant cyber incidents also could affect financial stability by interacting with and amplifying other financial system vulnerabilities such as leverage and run risk. This prospect is made more likely by the possible intentional nature of cyber events.
Recent Cyber Examples
While no incident has yet significantly impaired the financial system, we apply the framework to some recent examples to illustrate how a cyber incident may have greater impact.
The first example is a cyberattack directed at a bank holding company that impairs the firm's data. For example, in 2019, the data of more than 100 million Capital One customers were accessed after an attacker exploited a vulnerability in the firewall configuration of the bank's cloud-based infrastructure (Barrett 2020). A cyberattack that affects data at multiple large financial institutions could lead to a broad loss of confidence in the security of the financial sector. If the institutions' data are corrupted during the attack, the recovery process could be extensive.
The second example is a cyberattack on a financial market exchange that disrupts trading. In 2020, distributed denial of service attacks overwhelmed the website of New Zealand's Exchange (NZX) in 2020. The exchange had to halt trading in cash, debt, and derivatives for most of four days, which disrupted access to price information for assets only traded on its exchange. NZX was vulnerable because it lacked adequate defenses and a response playbook (FMA 2021). An attack that shuts down trading at a large and interconnected financial market exchange could disrupt price information more widely, as well as clearing and settlement, and trigger a loss of confidence.
An attack on a third-party vendor represents the third example. In 2020, a nation-state actor inserted malware into a routine update of network management software sold by SolarWinds, a third-party vendor. SolarWinds customers, which included large financial institutions, were infected by the malware when they installed the software update. The attack opened a backdoor through which attackers could have exploited the customers' computer systems. While financial institutions do not appear to have been the intended targets, if they had been, the outcome for financial stability could have been much worse, as the attackers reportedly had access to the computer systems for some time (FBI et al 2021).
Of course, cyber incidents can arise independent of any cybersecurity event, reflecting the challenges of managing the risks associated with digital operations. Three widely reported incidents illustrate the point. A cloud service provider experienced an outage of almost five hours because of software and configuration errors that occurred during routine maintenance (Google 2019). Had financial institutions been farther along in transitioning their business activities to the cloud, the outage could have disrupted the financial system more widely. A major bank providing payment and settlement services was unable to send or receive messages to direct payments for institutional customers over the Society for Worldwide Interbank Financial Telecommunication (SWIFT) funds-transfer network for a period of 19 hours (Burne 2016). Although alternatives to SWIFT and backup systems were used, the large volume of payments affected meant that many payments were delayed and the bank had a backlog to clear once service was restored. The outage started on a Sunday afternoon and was resolved early Monday. Had it started during the week or lasted longer, the disruption to payment flows could have affected other banks and disrupted financial institutions' funding. Finally, smoke in a large bank's data center caused an automatic shutoff of power to the center. Operations were re-routed to backup data centers, but some customer accounts remained inaccessible through online or mobile banking applications or ATMs (Moyer 2019). Whereas the previous two examples originated with problems in technology systems, which have greater potentially to be common across firms, smoke in a data center is a physical occurrence and thus more idiosyncratic in nature. Nevertheless, in today's financial system, physical and digital operations are heavily interconnected, and problems in either can affect the other.
Scope for Larger Effect
The examples above help illustrate how cyber incidents could have much larger systemic effects than seen so far. Another approach to understanding possible amplification comes from Eisenbach, Kovner and Lee (2021), which sought to quantify the effect of a hypothetical outage that prevents one of the five most active ("top-five") banks from sending payments for one day. As was seen in the payment disruptions around September 11, 2001, when one or more banks are unable to send payments over Fedwire, other banks can be indirectly affected. Those innocent bystander banks receive fewer payments from banks experiencing the outage and as a result may have trouble making payments themselves. Using data from 2018, the study found that, on average, 31 percent of the banking sector (excluding the directly affected bank) by assets would face compromised liquidity. The effect is smaller when estimated using 2020 data due to the increase in reserves; when banks have more reserves, the failure to receive payments is less likely to impair liquidity. Figure 1 shows the distribution of the effect on different days and for different top-five banks. The blue bars show the unweighted share of affected banks, meaning the percentage of banks for which, if a top-five bank stopped sending payments, that bank would see its reserve balances drop more than two standard deviations below the previous month's balance. The grey and red bars show the distribution weighted by bank assets, with the red bars showing the total effect and the grey showing the amplification, meaning the share of affected banks excluding the top five banks. If banks react intraday, payments exceeding 2.5 times daily real gross domestic product may not be processed. The majority of forgone payments support other financial market activity, so the original disruption could spread well beyond the top five banks.
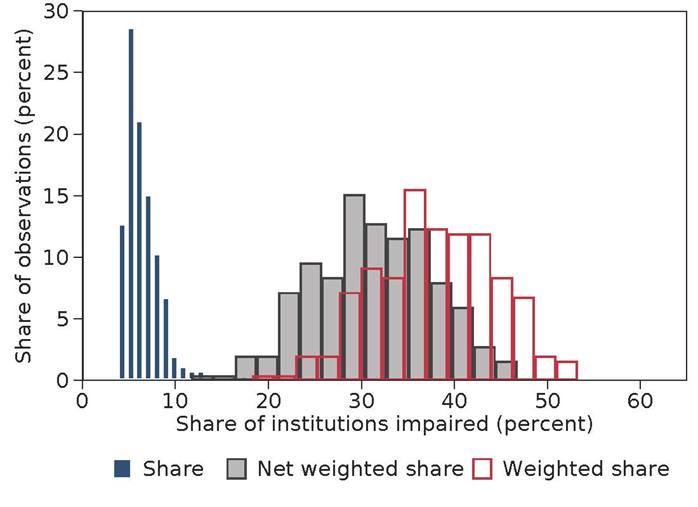
Note: Figure shows the distribution of the share of institutions with compromised liquidity positions under a hypothetical attack on a top-5 bank in Fedwire in 2018. The blue represents unweighted share; the red represents share weighted by bank assets; and the gray represents the weighted share excluding the top-5 bank that is assumed to be attacked.
Source: Eisenbach, Kovner, and Lee (2021)
The study also considered a similar hypothetical attack on a designated financial market utility (DFMU), such as the Clearing House Interbank Payments System (CHIPS) (large value payment system) or CLS (provider of foreign exchange settlement services). Figure 2 shows the dollars paid each day between banks and the DFMU. If banks were forced to redirect those payments, and thus forego the netting and payments efficiencies of using the DFMU, the additional required payments would require two to three times more liquidity to execute. It also seems likely that participants would reduce their activity in markets that are centrally cleared by an affected DFMU, meaning that the ramifications would disrupt market volumes and potentially lead to sudden price changes.
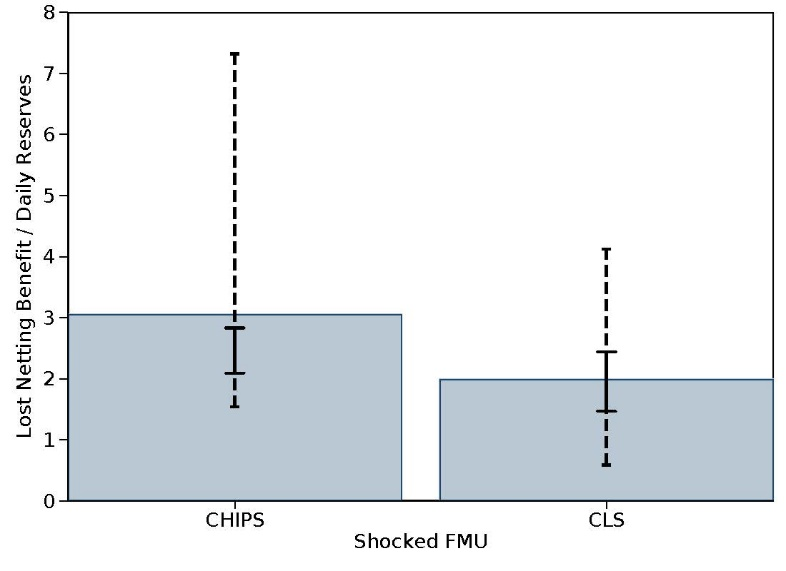
Note: Figure shows the distribution of estimated value of failed payments on CHIPS and CLS, scaled by daily reserve balances of each member bank of the DFMU. Bars represent the average ratio; solid whiskers represent the p25/p75 range; dashed whiskers the p1/p99 range.
Source: Eisenbach, Kovner, and Lee (2021)
Assessing Firm- and System-level Vulnerabilities
Cyber vulnerabilities can be measured and assessed at both the firm and system level. At the firm level, data on firms' cyber hygiene can point to relevant vulnerabilities, as well as areas of focus for risk management and controls to enhance resilience. The National Institute of Standards and Technology (NIST) has developed a framework for improving critical infrastructure cybersecurity that has been widely adopted by private and public sector organizations (NIST 2018). The framework identifies five functions that organize cybersecurity activities: Identify, Protect, Detect, Respond, and Recover. The Identify function involves identifying critical resources and their cybersecurity risks. Protect captures the ability to prevent potential cybersecurity events from succeeding at breaching or impairing systems. Detect covers the ability to discover cybersecurity events quickly. The Respond and Recover functions limit the effect of cyber events and restore any impaired capabilities. Each function has categories and subcategories on which firms' readiness could be assessed; trends in readiness over time can point to rising or diminishing vulnerabilities.
System-level vulnerabilities are system features that can amplify or spread a cyber incident and are generally more difficult to assess than those at the firm level. There are several sources of system-level vulnerabilities. Availability and accessibility vulnerabilities are one source and are associated with critical financial or IT services and data. These vulnerabilities are driven by the presence of dominant firms in financial markets and the supply chain, especially single points of failure, as well as the data dependence of financial system operations. Outages can disrupt payment flows and price discovery. The loss of data access or integrity can prevent the finality of trades if there is uncertainty about the custody of an asset. Such incidents can prove difficult to remedy because data must integrate with multiple applications within and across firms. Redundant services or systems can help mitigate risks, but plans for redundancy may lack full capability or fail in practice. For example, primary and backup systems can experience the same cyber incidents, and even when backup systems are available, financial institutions must be able to switch to them smoothly and quickly.
A second system-level vulnerability arises from the financial system's interconnectedness, and digital operations compound the number and complexity of linkages. As with traditional shocks to financial stability, interconnectedness can inhibit efforts to mitigate risk and amplify any cyber incident.
Third, when information asymmetries and gaps are present, cyber incidents can spread longer and do more damage because firms lack timely notice of incidents identified elsewhere in the system. Interconnectedness can interact with these information problems: even if firms learn of incidents elsewhere, they may not be aware of their own exposure to the underlying cyber event.
The role of trust and confidence in financial system relationships is the last source of system vulnerability. A loss of confidence can set off a domino effect, triggering potentially contagious runs and asset fire sales, even at institutions not directly affected.
Ample capital and liquidity in the system and the presence of cyber insurance may not adequately mitigate these system-level vulnerabilities. Capital can reduce the likelihood of solvency runs and other spillovers that occur when an institution fails. As such, capital can be a buffer against cyber-related losses and thus may contain some amplification, but it may not do much to speed up the restoration process. Further, many regulatory frameworks do not incorporate cyber risk in minimum capital requirements, so firms may be undercapitalized against the risk.
Data for Monitoring Vulnerabilities
While there is extensive ongoing supervisory attention to firm-level cyber resilience, data gaps remain, particularly for monitoring system-level vulnerabilities. At the firm level, consistent data on cyber incidents is needed. At the system level, measures of digital interdependencies and the speed with which backup systems and providers can be quickly enabled would be beneficial. Federal Reserve staff are working to help close these data gaps and to improve understanding of amplification through tabletop exercises and pre- and post-mortem studies of cyber events.
Additional Implications of Cyber Risk for Financial Stability
There are two important dimensions of cyber risk and financial stability not discussed here. First, the Federal Reserve plays a central role in financial markets and the payment system, providing critical infrastructure that supports both. Thus, an operational disruption, including one from a cyber event, could be extremely damaging. Second, financial stability vulnerabilities can arise from technological innovations. As cryptocurrencies and other fintechs evolve, new financial stability implications may emerge from increasing reliance on technology and reduced redundancy that may be important to consider.
This article also omits discussion of firm-level and industry efforts to address cyber risk that do not have a financial stability focus, although they reduce cyber vulnerabilities. For example, microprudential policies can reduce cyber risk, and cyber risks are the subject of significant supervisory attention. In addition, a number of industry groups, as well as the official sector, actively exchange information about cyber incidents and responses to mitigate risk.
Conclusion
This article describes how cyber risk both presents increasingly salient shocks and sources of vulnerabilities in the financial stability monitoring framework used in the Federal Reserve's Financial Stability Reports. Research to better understand the interconnectedness created by technological linkages and the risks posed to the financial system by decreasing redundancies, the digital supply chain, and malevolent actors is increasingly important as cyber risk continues to grow rapidly. Progress closing data gaps will improve the assessment of cyber vulnerabilities and identification of mitigants. In the meantime, better information sharing and a coordinated response to successful attacks can improve mitigation. Collaborative efforts within the official sector and joint with industry and academia also can increase understanding of the systemic dimensions of cyber risk, including the potential for the financial system to amplify the effect of a cyber event and the potential to mitigate the spillover effects.
References
Afonso, Gara, Filippo Curti, and Atanas Mihov (2019). "Coming to Terms with Operational Risk," Federal Reserve Bank of New York Liberty Street Economics, January 7, https://libertystreeteconomics.newyorkfed.org/2019/01/coming-to-terms-with-operational-risk/.
Barrett, Devlin (2020). "Capital One fined $80 million for 2019 hack of 100 million credit card applications," August 6, https://www.washingtonpost.com/national-security/capital-one-fined-2019-hack/2020/08/06/90c2c836-d7f3-11ea-aff6-220dd3a14741_story.html
Board of Governors of the Federal Reserve System November (2021). Financial Stability Report, pg. 3, https://www.federalreserve.gov/publications/files/financial-stability-report-20211108.pdf.
Burne, Katy (2016). "Bank of New York lost ability to process payments for 19 hours," The Wall Street Journal, Dec. 7, https://www.wsj.com/articles/bny-mellon-outage-caused-some-swift-payments-to-fail-this-week-1481149459.
Eisenbach, Thomas, Anna Kovner, and Michael Junho Lee (2021). "Cyber risk and the U.S. financial system: A pre-mortem analysis," Journal of Financial Economics, forthcoming.
Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency, Office of the Director of National Intelligence, and National Security Agency (2021). Joint statement, January 5, https://www.cisa.gov/news/2021/01/05/joint-statement-federal-bureau-investigation-fbi-cybersecurity-and-infrastructure.
Financial Markets Authority (FMA) (2021). "Market Operator Obligations Targeted Review – NZX," January, https://www.fma.govt.nz/assets/Reports/Market-Operator-Obligations-Targeted-Review-NZX.pdf.
Google Cloud (2019). Google Cloud Networking Incident #19009, Google Cloud Status Dashboard, June 6, https://status.cloud.google.com/incident/cloud-networking/19009.
Moyer, Liz (2019). "Wells Fargo says it is working to fully restore systems as outage spills into day two," Feb. 8, https://www.cnbc.com/2019/02/08/wells-fargo-says-working-to-fully-restore-system-as-outage-spills-into-day-2.html.
National Institute of Standards and Technology (NIST) (2018). "Framework for improving critical infrastructure cybersecurity," v. 1.1, April 16, https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf.
1. Kotidis and Schreft are with the Board of Governors of the Federal Reserve System. Brando, Kovner, and Lee are with the Federal Reserve Bank of New York. The views expressed in this article are the authors' alone and do not indicate concurrence by other members of the Federal Reserve System staff, the Board of Governors, or the Federal Reserve Bank of New York. Return to text
2. Cyber risk is consistently cited as a top risk in surveys of industry participants. See the DTCC 2021 Systemic Risk Barometer survey (https://www.dtcc.com/-/media/Files/Downloads/Thought-Leadership/26362-Systemic-Risk-2020.pdf), the Bank of England's 2021 H2 Systemic Risk Survey (https://www.bankofengland.co.uk/systemic-risk-survey/2021/2021-h2), and the Bank of Canada's Spring 2021 Financial System Survey (https://www.bankofcanada.ca/2021/05/financial-system-survey-highlights-spring-2021/). Return to text
3. No figures are available for the capital specifically reserved for cyber risk, which is currently accounted for as a subset of operational risk. However, for the largest bank holding companies, about 33 percent of regulatory capital is held against operational risk, compared with 66 percent for credit risk and 6 percent for market risk. See Afonso, Curti, and Mihov (2019). There are no liquidity requirements specific to operational risk. Return to text
4. Note that increased concentration may increase vulnerabilities in the financial system more generally, not just those associated with cyber risk, as the potential impact on the financial system of an operational risk event or a liquidity or solvency shock is larger when there are more single points of failure. Return to text
Brando, Danny, Antonis Kotidis, Anna Kovner, Michael Lee, and Stacey L. Schreft (2022). "Implications of Cyber Risk for Financial Stability," FEDS Notes. Washington: Board of Governors of the Federal Reserve System, May 12, 2022, https://doi.org/10.17016/2380-7172.3077.
Disclaimer: FEDS Notes are articles in which Board staff offer their own views and present analysis on a range of topics in economics and finance. These articles are shorter and less technically oriented than FEDS Working Papers and IFDP papers.